Cryptomomen.com – In today’s increasingly digital society, the convenience of public Wi-Fi has become indispensable. However, these open networks pose a significant threat to the security of cryptocurrency transactions, as they provide an easy access point for malicious actors to intercept sensitive data.
As cryptocurrency adoption continues to rise, understanding the dangers of public Wi-Fi and implementing secure connections is crucial to safeguard the integrity and safety of transactions.
Please continue reading to delve into the importance of secure connections for crypto transactions and explore the measures you can take to protect your digital assets while connected to public Wi-Fi networks.
Introduction
In the burgeoning world of cryptocurrency, maintaining the security of your digital assets is paramount.
Public Wi-Fi networks pose a significant risk, as they provide a foothold for malicious actors to intercept sensitive information.
Hackers can use techniques like packet sniffing, phishing, and malware to compromise your devices and steal your cryptocurrency.
To safeguard your funds, it’s crucial to avoid using public Wi-Fi for accessing cryptocurrency exchanges, conducting transactions, or storing private keys.
Instead, prioritize using secure, private networks or consider investing in a hardware wallet for offline storage.
Thank you for visiting Cryptomomen.com
Hook: The allure of public WiFi and its risks

The lure of public WiFi offers convenience but harbors hidden risks that cryptocurrency enthusiasts should be aware of.
Connecting to unsecured networks can expose sensitive financial data, making users vulnerable to phishing scams and malware attacks.
Unencrypted connections allow hackers to intercept and steal login credentials, transaction details, and even private keys.
By utilizing public WiFi, users inadvertently create an opportunity for malicious actors to exploit vulnerabilities.
To safeguard against these threats, it is vital to implement rigorous security measures, such as using a virtual private network (VPN) to encrypt data transmissions, regularly updating antivirus software, and exercising caution when accessing financial accounts on public networks.
Thesis statement: The necessity of secure connections for crypto transactions in public spaces
The prevalence of cryptocurrency transactions in public spaces necessitates the urgent implementation of secure connections to safeguard digital assets.
Public WiFi networks, while convenient, pose significant risks due to their susceptibility to malicious attacks and eavesdropping.
Interceptors can easily intercept unencrypted data transmitted over unsecured connections, leading to unauthorized access to cryptocurrency wallets and the potential theft of funds.
Therefore, individuals engaging in crypto transactions in public areas must prioritize secure connections through the use of virtual private networks (VPNs), secure sockets layer (SSL) certificates, and strong encryption protocols to protect the integrity and confidentiality of their financial transactions.
The Inherent Dangers of Public WiFi

Public WiFi networks provide convenient internet access, but they also pose inherent security risks.
First, unsecured networks allow attackers to intercept your data, including passwords and financial information.
Second, malicious hotspots can trick you into connecting to a network controlled by criminals.
These networks may track your online activity or redirect you to phishing websites.
Finally, public WiFi can be used to spread malware, which can infect your devices and compromise your data.
To mitigate these risks, consider using a virtual private network (VPN) or connecting to only trusted networks.
Unsecured networks: Lack of encryption and authentication
Public Wi-Fi hotspots and unsecured networks are breeding grounds for cyberattacks, due to the absence of encryption and authentication protocols.
The lack of these protective measures allows third parties to eavesdrop on unencrypted traffic, intercept sensitive data, and even inject malicious code into unsuspecting devices. This poses significant risks to individuals, especially when accessing online banking accounts or conducting sensitive transactions.
Cybercriminals often exploit such vulnerabilities to steal personal information, financial credentials, and even cryptocurrency assets. It is crucial for users to be aware of these risks and adopt robust security practices, such as using VPNs, strong passwords, and two-factor authentication, to protect themselves from potential threats lurking on unsecured networks.
Man-in-the-Middle (MitM) attacks: Interception and manipulation of data
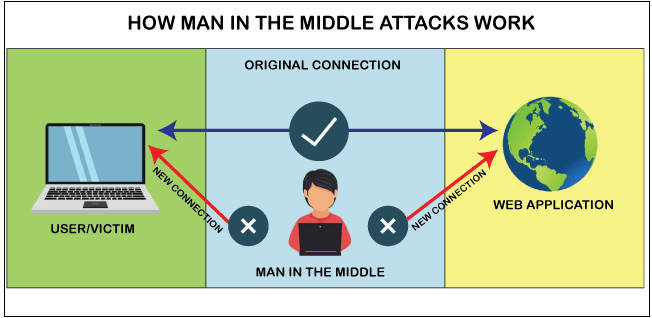
In a man-in-the-middle attack, an adversary intercepts communication between two parties and manipulates the data transmitted. This technique is commonly employed in public Wi-Fi environments, where attackers can easily establish their own access points and pose as legitimate networks.
Once connected, they can monitor and alter data exchanged between users and websites or other parties, potentially leading to sensitive information theft or financial fraud.
Cryptocurrency transactions are particularly vulnerable to MitM attacks, as they often take place over unencrypted channels. Furthermore, the anonymity inherent in cryptocurrency transactions can make it challenging to identify and prosecute attackers.
Phishing scams: Malicious websites disguised as legitimate ones
Beware of phishing scams that lurk in the shadows, cleverly disguised as legitimate websites. These malicious portals aim to steal your cryptocurrency by mimicking familiar platforms. To protect yourself, double-check the URL, look for HTTPS, and be wary of unsolicited emails requesting personal information.
FAQs:
- How can I spot a phishing scam?
Check the URL for any inconsistencies or misspellings compared to the legitimate site. - What should I do if I encounter a phishing scam?
Report it immediately to the platform and disregard any requests for personal information. - Can I recover my stolen cryptocurrency?
Unfortunately, once stolen, it’s challenging to retrieve cryptocurrency. Hence, it’s crucial to remain vigilant and protect your assets.
Specific Crypto-Related Threats
Cryptosecurity concerns: Cryptocurrency poses unique risks, such as online scams, phishing, and hacking.
When accessing crypto platforms or wallets on public Wi-Fi, use a VPN or cellular data to encrypt your connection.
Be cautious of suspicious emails or ads claiming to offer free crypto.
Store your passwords securely and enable two-factor authentication on all accounts related to cryptocurrency.
Theft of private keys: Vulnerability of wallets to unencrypted networks
![4. Keys, Addresses, Wallets - Mastering Bitcoin [Book]](https://www.oreilly.com/api/v2/epubs/9781491902639/files/images/msbt_0411.png)
Unavoidably, cryptocurrency wallets are vulnerable to theft when connected to unencrypted networks.
The unencrypted nature of public Wi-Fi hotspots creates an open door for malicious actors to intercept private keys and drain funds from unsuspecting victims.
Transaction manipulation: Alteration of transaction details during transmission
Transaction manipulation, the illicit alteration of transaction details during transmission, is a prevalent threat in the realm of cryptocurrency security.
This nefarious activity often occurs on public Wi-Fi networks, where attackers can intercept and modify data transmitted between devices.
By leveraging specialized tools, hackers can manipulate transaction details, such as the amount, recipient address, or sender information, resulting in unauthorized transfers of funds.
To mitigate this risk, it is imperative to exercise caution when conducting cryptocurrency transactions on public Wi-Fi networks.
Utilizing a virtual private network (VPN) or a dedicated mobile hotspot can significantly enhance security by encrypting data and preventing unauthorized access.
Additionally, employing multi-factor authentication and using reputable cryptocurrency exchanges with robust security protocols can further safeguard transactions from malicious manipulation.
Hope it is useful
In conclusion, navigating the realm of cryptocurrency transactions demands utmost vigilance against potential threats.
Public WiFi networks, while convenient, pose significant risks that can compromise your digital assets.
Employing secure connections, such as VPNs, is paramount to safeguard your sensitive information and prevent malicious actors from intercepting your transactions.
By adhering to these cybersecurity best practices, you can minimize the vulnerabilities associated with public WiFi and ensure the safety of your cryptocurrency.
Thank you for reading, and don’t forget to share this invaluable information with others.